On-Demand: WiFi Pentesting Bootcamp
Write your awesome label here.
Subscribe to access bootcamp recordings and more!
Accessible via our AttackDefense lab platform
Upon logging in to the AttackDefense lab platform, annual subscribers will be able to access recordings of all our on-demand bootcamps and associated labs.
Who is this bootcamp for?
1. Anyone wanting to enter the industry as a network pentester
2. WiFi security enthusiasts and beginners
3. Suitable for beginners – all you need is a laptop and basic working knowledge of Linux.
2. WiFi security enthusiasts and beginners
3. Suitable for beginners – all you need is a laptop and basic working knowledge of Linux.
Prerequisites
1. A basic knowledge of computers and networking
2. Familiarity with the Linux operating system
Course reviews
Charles Faes
Network and Security Engineer, Belgium
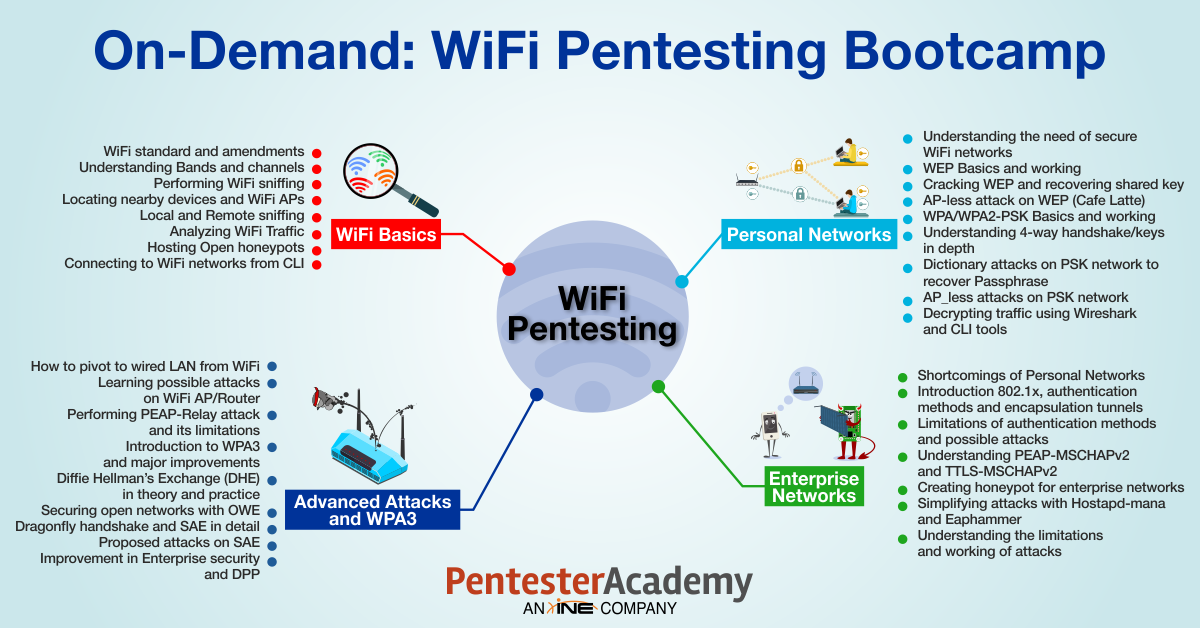
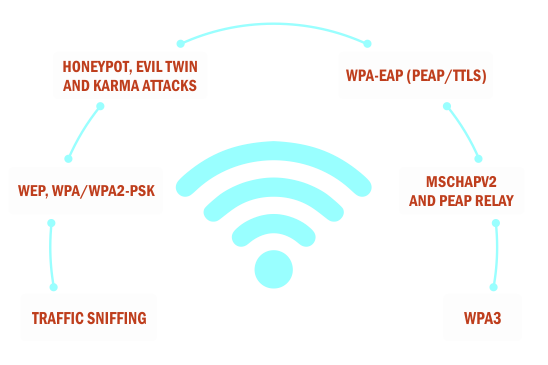
Module I: Protocol Basics, Traffic Sniffing, and Recon
-
WiFi standard basics
-
Bands
-
Channels
-
SSID
-
BSSID
-
Frame structure and header
-
Transmission basics
-
Basic commands to interact with WiFi interface
-
Traffic sniffing
-
WiFi traffic sniffing
-
Monitor mode
-
Remote sniffing
-
Capturing and storing traffic
-
Discovering wireless networks and clients
-
Analyzing WiFi traffic (header/packet analysis)
Module II: Attacking Personal Networks
-
Introduction to WiFi security schemes
-
WEP
-
WEP-40
-
WEP-104
-
Encryption-based
-
WPA (TKIP)
-
WPA2 (CCMP)
-
Management modes
-
Personal Network (PSK)
-
Enterprise network (EAP or MGT)
-
Observing the difference in packets
-
Lab 3 mentioned in module I
-
Cracking WEP
-
Theory and explanation
-
Live WEP cracking
-
Decrypting WEP traffic
-
Cracking WPA/WPA2-PSK
-
Theory and explanation
-
Live WPA-PSK cracking
-
Decrypting WPA-PSK traffic
-
AP-less Attacks
Module III: Attacking Enterprise Networks
-
Understanding WPA/WPA2-EAP
-
PEAP
-
GTC
-
MSCHAPv2
-
TTLS
-
PAP
-
MSCHAPv2
-
Honeypot attacks
-
Creating fake networks
-
Evil twin attack
-
Karma attacks
-
Attacking WPA/WPA2-PEAP
-
Theory and explanation
-
PEAP-GTC
-
PEAP-MSCHAPv2
-
Attacking WPA/WPA2-TTLS
-
Theory and explanation
-
TTLS-PAP
-
TTLS-MSCHAPv2
Module IV: Advanced Attacks and WPA3
-
PEAP-relay attack
-
WiFi pivoting
-
Introduction to WPA3
-
WPA3-OWE (Opportunistic Wireless Encryption)
-
WPA3-SAE (Simultaneous Authentication of Equals)
-
WPA3-SAE Transition Mode
-
WPA3-Enterprise
-
Proposed attacks on WPA3
Meet the instructor
Nishant Sharma
Nishant Sharma leads R&D at Pentester Academy and Attack Defense. He has 8+ years of experience in the information security field including 6+ years in WiFi security research and development. He has presented research and conducted workshops at Blackhat USA/Asia, DEF CON China, HITB, RootCon, Packet Hacking Village, Wireless Village, IoT village and Demo labs (DEFCON USA).
Nishant’s Twitter handle is also @wifisecguy, which should tell you all you need to know about his research interests.
Nishant’s Twitter handle is also @wifisecguy, which should tell you all you need to know about his research interests.
Nishant Sharma - Instructor
Get informed about future bootcamps!
Thank you!