Pentesting with Metasploit: Beginner Edition
Familiarize yourself with how to use Metasploit to its full extent while performing pentesting on Windows and Linux machines.
Write your awesome label here.
Build Your Cybersecurity Credentials
Live Session Schedule
Prerequisites
1. A basic knowledge of computers and networking
2. Familiarity with any Linux and Windows OS
2. Familiarity with any Linux and Windows OS
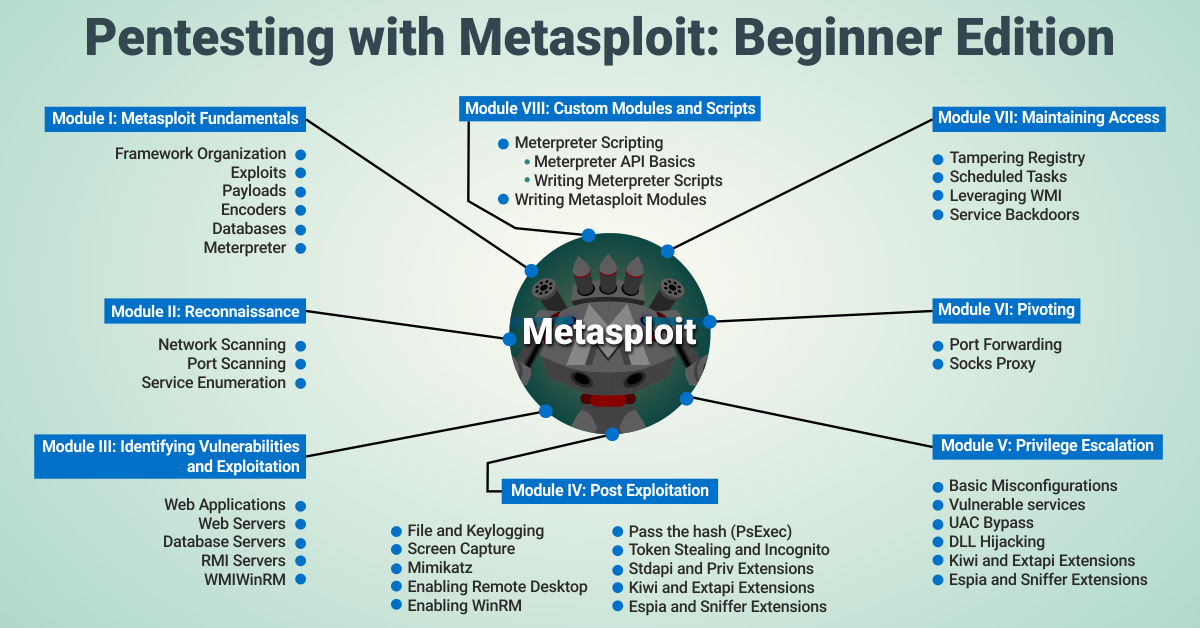
Module I: Metasploit Fundamentals
-
Framework Organization
-
Exploits
-
Payloads
-
Encoders
-
Databases
-
Meterpreter
Module II: Reconnaissance
-
Network Scanning
-
Port Scanning
-
Service Enumeration
Module III: Identifying Vulnerabilities and Exploitation
-
Web Applications
-
Web Servers
-
Database Servers
-
RMI Servers
-
WMI
-
WinRM
Module IV: Post Exploitation
-
File and Keylogging
-
Screen Capture
-
Mimikatz
-
Enabling Remote Desktop
-
Enabling WinRM
-
Pass the hash (PsExec)
-
Token Stealing and Incognito
-
Stdapi and Priv Extensions
-
Kiwi and Extapi Extensions
-
Espia and Sniffer Extensions
Module V: Privilege Escalation
-
Basic Misconfigurations
-
Vulnerable services
-
UAC Bypass
-
DLL Hijacking
-
Kiwi and Extapi Extensions
-
Espia and Sniffer Extensions
Module VI: Pivoting
-
Port Forwarding
-
Socks Proxy
Module VII: Maintaining Access
-
Tampering Registry
-
Scheduled Tasks
-
Leveraging WMI
-
Service Backdoors
Module VIII: Custom Modules and Scripts
-
Meterpreter Scripting
-
Meterpreter API Basics
-
Writing Meterpreter Scripts
-
Writing Metasploit Modules
Meet the instructor
Jeswin Mathai
He has published his work at DEFCON China, RootCon, Blackhat Arsenal, and Demo labs (DEFCON). He has also been a co-trainer in classroom trainings conducted at HITB, RootCon, OWASP NZ Day. He has a Bachelor degree from IIIT Bhubaneswar. He was the team lead at InfoSec Society IIIT Bhubaneswar in association with CDAC and ISEA, which performed security auditing of government portals, conducted awareness workshops for government institutions. His area of interest includes Malware Analysis and Reverse Engineering, Cryptography, WiFi security, and Web Application Security.
Jeswin Mathai - Instructor
Can't attend this bootcamp? Get informed about future bootcamps!
Thank you!