Attacking and Defending Active Directory: Advanced Edition
Build expertise in attacking and defending real-world enterprise Active Directory environments. Identify and analyze threats and practice attacks against a modern multi-forest Active Directory environment.
Write your awesome label here.
Build Your Cybersecurity Credentials
Live Session Schedule
Prerequisites
1. A good understanding of Active Directory security.
2. The ability to use command line tools.
2. The ability to use command line tools.
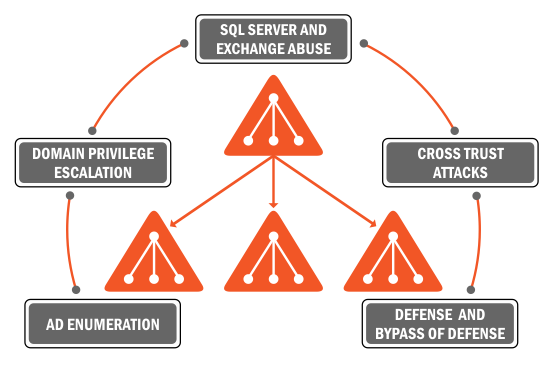
The course is split in four modules across four weeks:
Module I:
-
Introduction to Active Directory, attack methodology and tradecraft
-
Domain Enumeration (Attacks and Defense)
-
Enumerating information that would be useful in attacks with leaving minimal footprint on the endpoints
-
Understand and practice what properties and information to look for when preparing attack paths to avoid detection
-
Enumerate trust relationships within and across forests to map cross trust attack paths
-
Learn and practice escalating to local administrator privileges in the domain by abusing OU Delegation, Restricted Groups, LAPS, Nested group membership and hunting for privileges using remote access protocols
-
Credential Replay Attacks
Module II:
-
Abusing on-prem MS Exchange for privilege escalation and extracting emails and sensitive information from mailboxes
-
Evading application whitelisting (WDAC)
-
Domain Privilege Escalation by abusing Unconstrained Delegation: understand how unconstrained delegation is useful in compromising multiple high privilege servers and users in AD
-
Abusing Constrained Delegation for Domain Privilege Escalation by impersonating high privilege accounts
-
Using ACL permissions to abuse Resource-based Constrained Delegation
-
Domain Persistence Techniques
Module III:
-
Advanced Cross Domain attacks. Learn and practice attacks that allow escalation from Domain Admins to Enterprise Admins by abusing MS Products and delegation issues
-
Lateral movement from on-prem to Azure AD by attacking Hybrid Identity infrastructure
-
Advanced Cross Forest attacks. Execute attacks like abuse of Kerberoast, SID Filtering misconfigurations etc. across forest trusts forests and understand the nuances of such attacks
Module IV:
-
Abusing SQL Server for cross forest attacks
-
More on advanced Cross Forest attacks like abuse of Foreign Security Principals, ACLs etc.
-
Abusing PAM trust and shadow security principals to execute attacks against a managed forests
-
Detections and Defenses (Red Forest, JEA, PAW, LAPS, Selective Auth, Deception, App Whitelisting, ATA, Tiered Administration)
-
Bypassing defenses like Advanced Threat Analytics, Protected Users Group, WDAC etc.
Meet the instructor
Nikhil Mittal
Nikhil Mittal is a hacker, infosec researcher, speaker and enthusiast.
His area of interest includes red teaming, active directory security,
attack research, defense strategies and post exploitation research. He
has 12+ years of experience in red teaming.
He specializes in assessing security risks at secure environments that require novel attack vectors and "out of the box" approach. He has worked extensively on Active Directory, Azure AD attacks, defense and bypassing detection mechanisms and Offensive PowerShell for red teaming. He is creator of multiple tools like Nishang, a post exploitation framework in PowerShell, Deploy-Deception a framework for deploying Active Directory deception and RACE toolkit for attacking Windows ACLs. In his spare time, Nikhil researches on new attack methodologies and updates his tools and frameworks.
Nikhil has held trainings and bootcamps for various corporate clients (in US, Europe and SE Asia), and at the world’s top information security conferences. He has spoken/trained at conferences like DEFCON, BlackHat, BruCON and more.
He blogs at https://www.labofapenetrationtester.com/
He specializes in assessing security risks at secure environments that require novel attack vectors and "out of the box" approach. He has worked extensively on Active Directory, Azure AD attacks, defense and bypassing detection mechanisms and Offensive PowerShell for red teaming. He is creator of multiple tools like Nishang, a post exploitation framework in PowerShell, Deploy-Deception a framework for deploying Active Directory deception and RACE toolkit for attacking Windows ACLs. In his spare time, Nikhil researches on new attack methodologies and updates his tools and frameworks.
Nikhil has held trainings and bootcamps for various corporate clients (in US, Europe and SE Asia), and at the world’s top information security conferences. He has spoken/trained at conferences like DEFCON, BlackHat, BruCON and more.
He blogs at https://www.labofapenetrationtester.com/
Nikhil Mittal - Principal Instructor
Can't attend this bootcamp? Get informed about future bootcamps!
Thank you!